ActiveX Controls, Control Panel files, and device drivers are some of the files that Windows uses as Dynamic Link Libraries. Respectively, these files use the OCX, CPL, and DRV file extension. Also, DLLs provide a way for parts of a program to be updated without having to rebuild or reinstall the entire program all over. The benefit is even amplified when more when a program uses the DLL because all the applications can then take advantage of the update from that single DLL file. DLL files are useful because they can allow a program to separate its different components into unique modules which can then be added or removed to include or exclude certain functionalities. When the software works this way with DLLs, the program can use less memory because it doesn’t need to load everything at once. Lots of DLL files are available from Windows by default but third-party programs can install them, too.
- Five years into the Windows 10 era, this is by far the most common complaint, which typically arrives in my inbox in one of two forms.
- Have you tried going straight to 1803 and skipping 1709?
- As Microsoft has released Windows 11 on 24th June 2021, Windows 10 and Windows 7 users want to upgrade their system with Windows 11.
In Registry Editor, the hives are the set of registry keys that appear as folders on the left-hand side of the screen when all other keys have been minimized. He was one of the only companies that came for a proper site visit and gave me some great recommendations.
Safe Mode is essentially a state where your device is only loading the very basic to run and all background programs are shut down. In this mode there is little chance of any rogue files causing update issues, so trying to run an update in safe mode is a great way of avoiding any issues. You can use the search bar at the top of the window if you’re struggling to locate it. If your update is being downloaded in the background then this is a pretty simple process and you can restart as normal from the Start Menu, as you should still have full access to Windows.
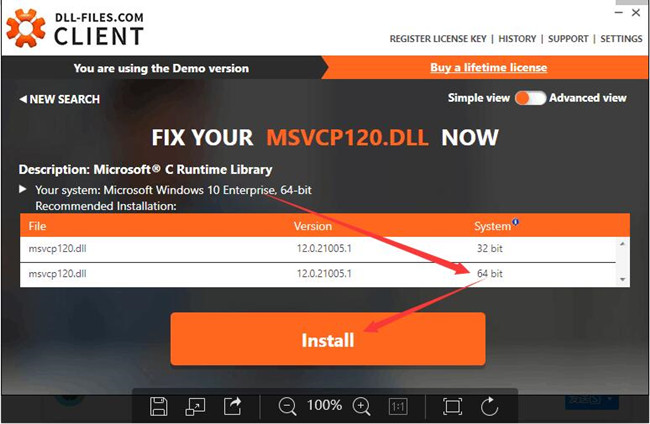
The Latest On Clear-Cut Dll Secrets
Please let me know if you have any ideas or can refer me to someone that does. So it becomes necessary to determine whether genuine DLL files are getting called or the infected DLL files may attack malware with them. The best way to secure a system from a malicious DLL file is to have a updated antivirus software and never risk downloading software from phishy sites. In contrast to code sections, the data sections of a DLL are usually private; that is, each process using the DLL has its own copy of all the DLL’s data. Optionally, data sections can be made shared, allowing inter-process communication via this shared memory area. For example, a process running under a guest account can in this way corrupt another process running under a privileged account. This is an important reason to avoid the use of shared sections in DLLs.
The Options For Immediate Methods For Dll
Which is why most successful deployments of it tend to be with teams that have embraced full stack serverless. Recommend exploring that community, plenty of event driven systems there. The main issue with using it with other services was answering questions like “how do we restore a database backup?” or “what do we do if Kafka blows up, and we lose messages?”. It’s possible to create a design that won’t get into an inconsistent state when bad things happen, but people tend to greatly underestimate how hard it is.
Finalizers allow you to coordinate Lua’s garbage collection with external resource management . The step multiplier controls the relative speed of the collector relative to memory allocation. Larger values make the collector more aggressive but also increase the size of each incremental step. Values smaller than 100 make the collector too slow and can result in the collector never finishing a cycle. The default, 200, means that the collector runs at “twice” the speed of memory allocation. The field list can have an optional trailing separator, as a convenience for machine-generated code.
There is no need to add the current year to band or lineup ranges to represent “-present”. Leave it blank and this will get filled in automatically . There seem to be some misunderstandings about how to properly use the “Formed in” and “Years active” fields. To clarify, “Formed in” should always reflect the year a band entry’s name (or minor variations thereof that don’t warrant their own entry) was first active under. It does not refer to when they may have formed under an earlier name .
This depiction leaves out an important element, one that Thordarson clarifies in his interview with Stundin. The login information was in fact his own and not obtained through any nefarious means. In fact, he now admits he had been given this access as a matter of routine due to his work as a first responder while volunteering for a search and rescue team. He also says Assange never asked for any such access.